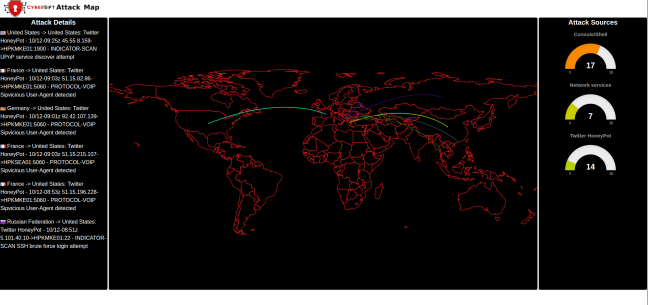
Recently we launched a small site called the "CyberSift Attack Map" hosted at http://attack-map.cybersift.io. Any one involved in the InfoSec industry will be instantly familiar with the site: It's basically a map of attacks which either trip some rule in a signature based IPS such as SNORT, or land in a honeypot. In this article we'll list … Continue reading How we built the CyberSift Attack Map
How we built the CyberSift Attack Map

You must be logged in to post a comment.